The Microsoft 365 Defender Research Team has revealed that it discovered a security vulnerability in macOS Monterey. This is the 2nd time the Redmond company discovered a security issue in macOS, after the Shrootless vulnerability, that came to light in October 2021.
What is the Powerdir vulnerability?
It is a security loophole that impacts a component in macOS called Transparency, Consent, and Control (TCC). This technology prevent apps from accessing the user's personal data like the iCloud, Calendar, as well as hardware such as the camera, microphone and location.
Apple had a security feature in place to restrict apps from accessing TCC, this policy only allowed apps with full disk access to make changes. Microsoft's researchers discovered that changing the home directory of a user, and spoofing a fake TCC database in its place, was enough to allow apps to bypass TCC's protection and compromise the data it should have protected. This exploit could have potentially be used for targeted attacks, e.g. a hacker could install replace an app with a malicious one to record private conversations, take screenshots of the user's screen, aka spy on the user.
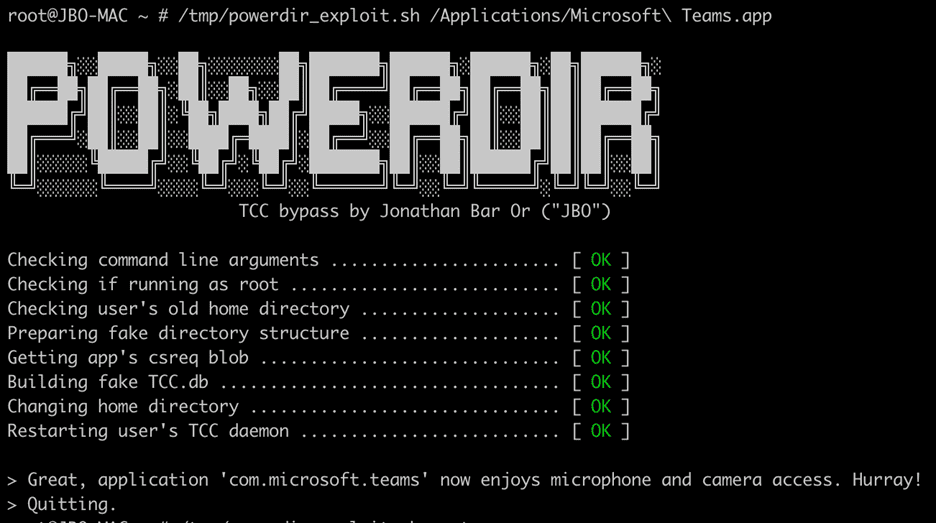
The above screenshot, from Microsoft's team, shows a proof-of-concept exploit to highlight how the Powerdir vulnerability was successful in gaining access to the user data. This is not the first time TCC has been found to be vulnerable, writes, Jonathan Bar Or, Senior Security Researcher at Microsoft. He notes that three such TCC related issues, namely Time Machine mounts (CVE-2020-9771), Environment variable poisoning (CVE-2020-9934), and Bundle conclusion issue (CVE-2021-30713), were patched by Apple since 2020. The report goes on to state that Microsoft was aware of other similar exploits, but these had been fixed by Apple, but when testing a fix for one of these, the researchers stumbled upon a new bug, Powerdir. Interestingly, the researchers had to update their proof-of-concept exploit, after a macOS update prevented the initial version from working.
Having confirmed that the bug in TCC could be exploited, Microsoft's Security Researchers shared their findings with Apple in July 2021, via Coordinated Vulnerability Disclosure (CVD), to allow the Cupertino company to patch the issue. Bleeping Computer notes that Microsoft collaborated with NETGEAR last year, to resolve critical bugs in the firmware of some router models, that hackers could have used to breach enterprise networks. It is good to see tech giants working together to protect users, but we have also seen independent security experts contribute to the ecosystem for the same cause.
Powerdir vulnerability has been patched in macOS 12.1 Update
Apple released the macOS 12.1 Update in December 2021, and this software update includes fixes for several security issues that were reported by researchers, and it includes a patch for the Powerdir vulnerability. The issue has been assigned the tag CVE-202-30970. Apple's Security Advisory mentions the Powerdir vulnerability's impact as" A malicious application may be able to bypass Privacy preferences." The description for the patch says that a logic issue was addressed with improved state management.
The vulnerability has also been patched in macOS Big Sur 11.6.2.
If you have not updated your macOS, you should install the patch as soon as possible.
Thank you for being a Ghacks reader. The post Microsoft says Powerdir vulnerability in macOS could have given attackers access to user data appeared first on gHacks Technology News.


0 Commentaires