Twitter announced this week that it will turn off SMS-based two-factor authentication on the site for most users. Only Twitter Blue subscribers may continue using two-factor authentication through SMS text messages after the March 20, 2023 deadline.
Twitter users who use SMS as the two-factor authentication method at the moment may disable it manually, or have it disabled by Twitter on March 20, 2023. Twitter recommends that users switch to another authentication option. The service supports two additional two-factor authentication methods that require an authentication app or a security key.
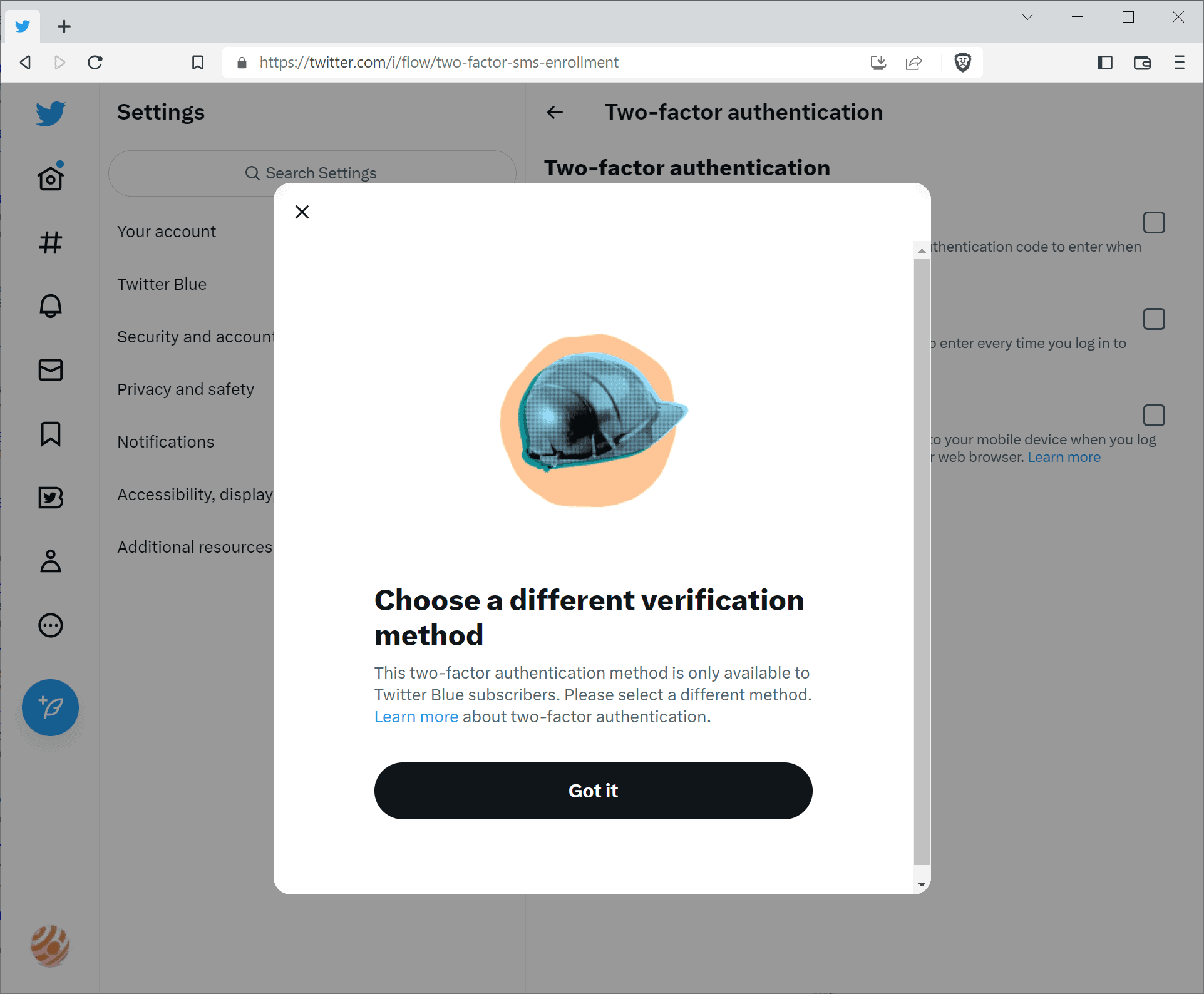
Twitter users who select Text message as the two-factor authentication option receive a prompt that asks them to choose a different verification method, as it is "only available to Twitter Blue subscribers".
Twitter Blue was turned into a subscription service in late 2022. Users and organizations pay $8 per month, or $11 per month on iOS, to get the blue checkmark on the site and some privileges associated with it.
Two-factor authentication adds a second layer of verification to the sign-in process. Instead of signing in with the username and password, users will also have to enter a code that they generate or receive using a support method. Text-based verification is very common, as it means receiving the code as a new SMS on a mobile device.
Twitter argues that phone-number based two-factor authentication has been "used - and abused - by bad actors". It is unclear what the company means by that specifically.
Here is what the change means for regular Twitter users, who use text messages as the two-factor authentication method. The feature works until March 20, 2023. The feature is disabled by Twitter on the deadline day automatically, making these accounts less secure than they were before. Twitter notes that associated phone numbers are not automatically removed from the accounts, but that users may do so in the settings.
How to set up two-factor authentication on Twitter
Twitter users who rely on two-factor authentication protection may want to disable the text message two-factor authentication option before March 20, 2023 to switch to another.
There are two alternatives available: authentication app or security key. Most may select authentication app, as they may not have access to a security key. Companies like Yubico have a range of security key products that Twitter users could use for that.
As for authentication apps, options include Google Authenticator, Microsoft Authenticator and Authy among many others.
Here is how you set up two-factor authentication on the site (website only, may be different in Twitter's mobile apps)
- Open the Twitter website and sign-in to the account.
- Select the three-dots menu and then Settings and Support > Settings and privacy.
- Select Security and account access > Security > Two-factor authentication.
- Select either Authentication app or Security key, depending on what is available or your preference.
- Follow the instructions to set up the feature. Note that this requires entering the Twitter password first to verify account ownership.
- If Authentication app is selected, it is necessary to link the app with the Twitter account by scanning a QR code and entering authentication code generated by the authentication app. This pairs the app with the account.
You may check out this support article on Twitter for detailed instructions.
Closing Words
Twitter is making the site deliberately less secure for non-Twitter Blue users who use text message two-factor authentication. Some may switch to another method, but there will likely also be users who won't enable another two-factor authentication method. The "abuse" argument by Twitter does not really make sense, as Twitter Blue users may continue to use text message authentication. It may have something to do with Twitter cutting costs everywhere to make the service profitable.
Now You: what is your take on this?
Thank you for being a Ghacks reader. The post Twitter disables SMS Two-Factor Authentication for most users on March 20, 2023 appeared first on gHacks Technology News.

0 Commentaires