Hackers Start Using Havoc Post-Exploitation Framework in Attacks
The one thing we’ve seen with these threat actors and hackers is that they seem to evolve to find loopholes in any new type of software. When you take away one tool, they just simply find another one to substitute that one. I personally haven’t fallen victim to this, but the one thing I have seen with the victims is that they are devasted by these cyber attacks.

Cyber attacks have been around for years, and they always seek to compromise your network, computer system, or device, by exploiting any weaknesses or vulnerabilities.
Cyber attacks are performed with a wide range of motives, such as activism, espionage, and commonly financial gain. The common forms of cyber-attacks are malware, phishing, denial-of-service attacks, man-in-the-middle attacks, zero-day exploits, and SQL injection.
The most common ways to protect against cyber attacks include having strong measures such as antivirus software, firewalls, security protocols, and intrusion detection systems. Well, despite all this, hackers have found a new loophole.
Security researchers have seen a recent switch to the new open-source control and command (C2) framework known as Havoc. Havoc is an alternative to paid options such as Brute Ratel and Cobalt Strike. Havoc is a cross-platform that can bypass Microsoft Defender on any up-to-date Windows 11 device. It does this by using sleep obfuscation, indirect syscalls, and return address spoofing.
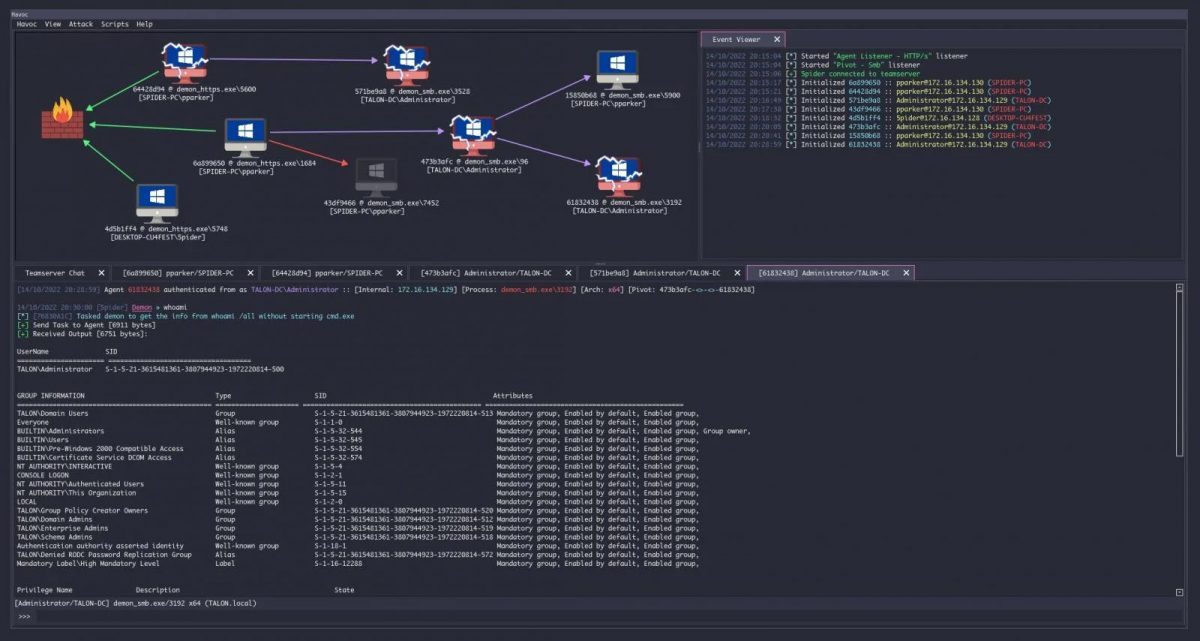
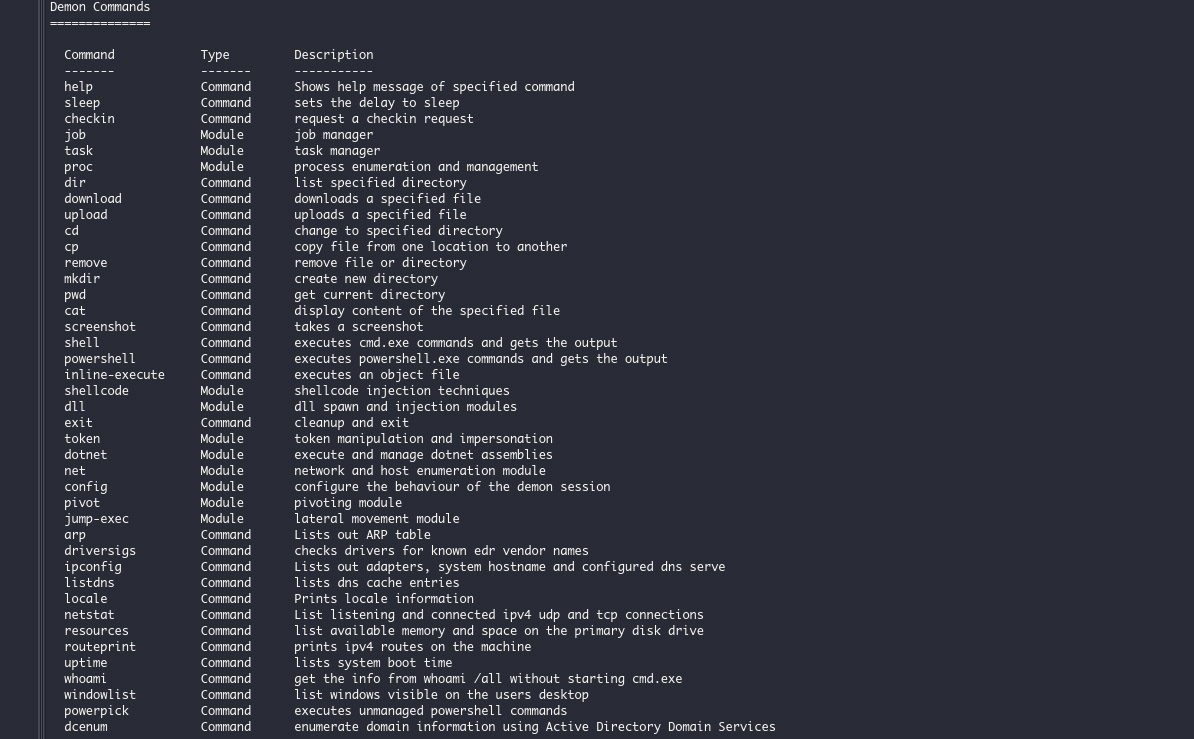
The hacker does this through a web-based management console that allows them to see any compromised devices and output from tasks and events. Similar to other exploitation kits Havoc works by incorporating a wide variety of models that allow hackers and pen testers to exploit devices by performing various tasks. The hacker code downloads additional payloads, executes command managing processes, executes shell codes, and manipulates Windows tokens.
How They Did It
The group of attackers remains unknown but recently a deployment of a post-exploitation kit in early January was part of an attack campaign that targeted an undisclosed government organization. The framework was released using a malicious npm package (Aabquerys) typosquatting module.
Zscaler ThreatLabz discovered through their research team that spotted that the shellcode loader dropped on any compromised systems disabling Event Tracing for Windows (ETW). This means the final Havoc Demon could be loaded without NT and DOS headers to avoid any detection.
Other Alternatives to Cobalt Strike
More Cobalt Strike alternatives have been deployed. Cobalt Strike has become a very common tool that is used by hackers to drop attacks on victims. These networks can be later breached for the delivery of additional malicious payloads and movements. Since defendants are also getting better at stopping and detecting these attacks, alternatives, have become essential for these threat actors.
According to Bleeping Computer, the other options that assist in invading antiviruses are Response (EDR) solutions such as Brute Ratel and Silver. Brute Ratel is an exploitation toolkit that was developed to detect attacks suspected to be linked to any Russian Sponsored hacking group APT 29 (CozyBear). As hackers seem to get better and better, defendants continue to work tirelessly.
Thank you for being a Ghacks reader. The post Hackers Start Using Havoc Post-Exploitation Framework in Attacks appeared first on gHacks Technology News.

0 Commentaires